TrustX to Splunk Cloud
TrustX application logs can be received into a security information and event management (SIEM) system using the TrustX API and Splunk Cloud. This guide will describe the necessary steps to ingest TrustX audit logs into Splunk Cloud using a Python script and HTTP Event Collector (HEC). The script pulls logs via the TrustX API and pushes them to Splunk.
Step 1 - Generate API Key in TrustX
In this section, an API key with the necessary permissions will be generated in the TrustX Backoffice.
- Log in to the TrustX Backoffice and navigate to the API Keys page found in the left-side vertical navigation bar.
- Click the 'New API Key' button to create a new API Key.
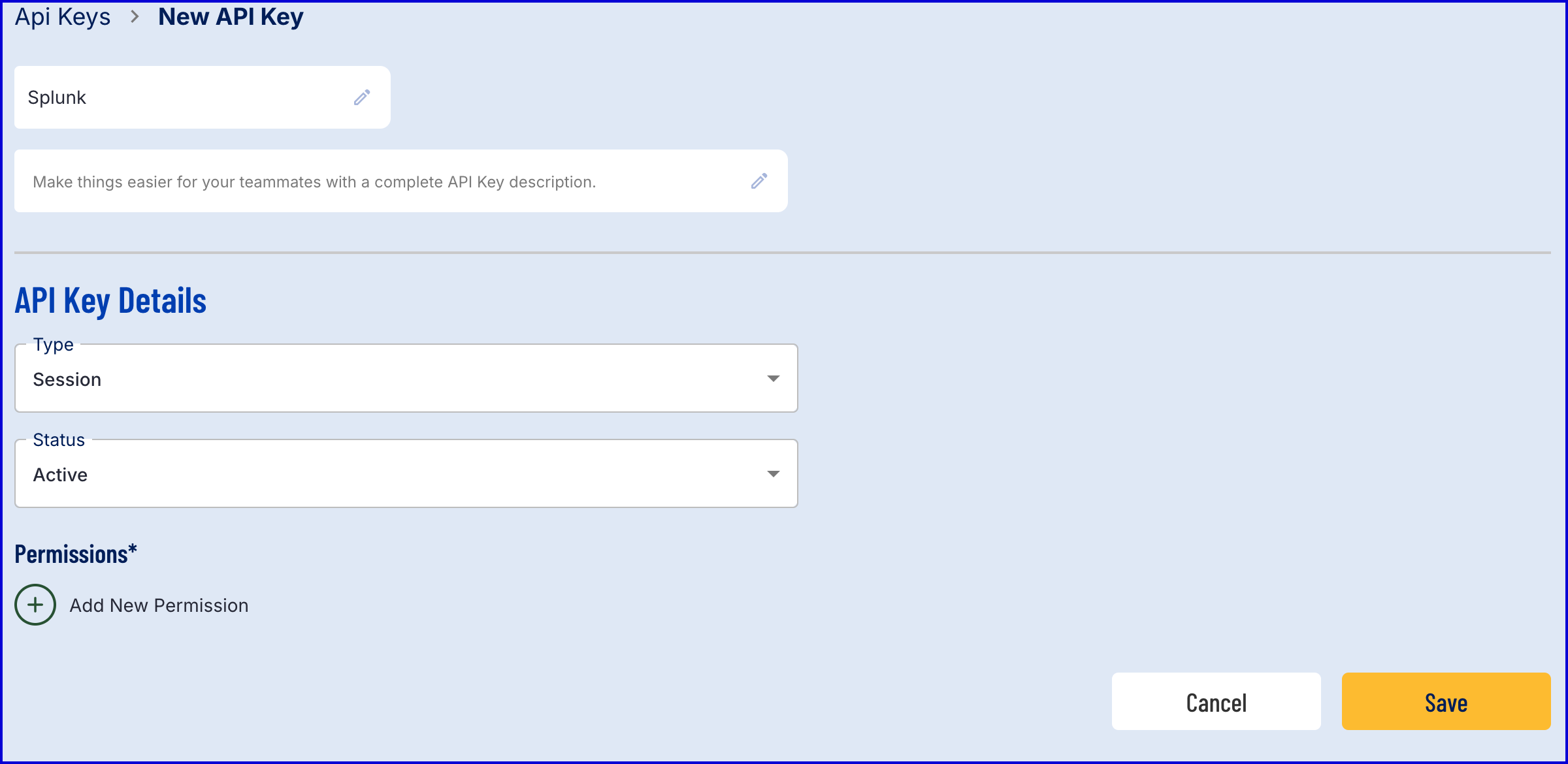
Configure the API Key such that the Type is Permanent and includes the following permissions:
- TNT#<your tenant>#MetricsServer:startAuditQuery
- TNT#<your tenant>#MetricsServer:getAuditQueryStatus
- TNT#<your tenant>#MetricsServer:getAuditQueryResults
Example:
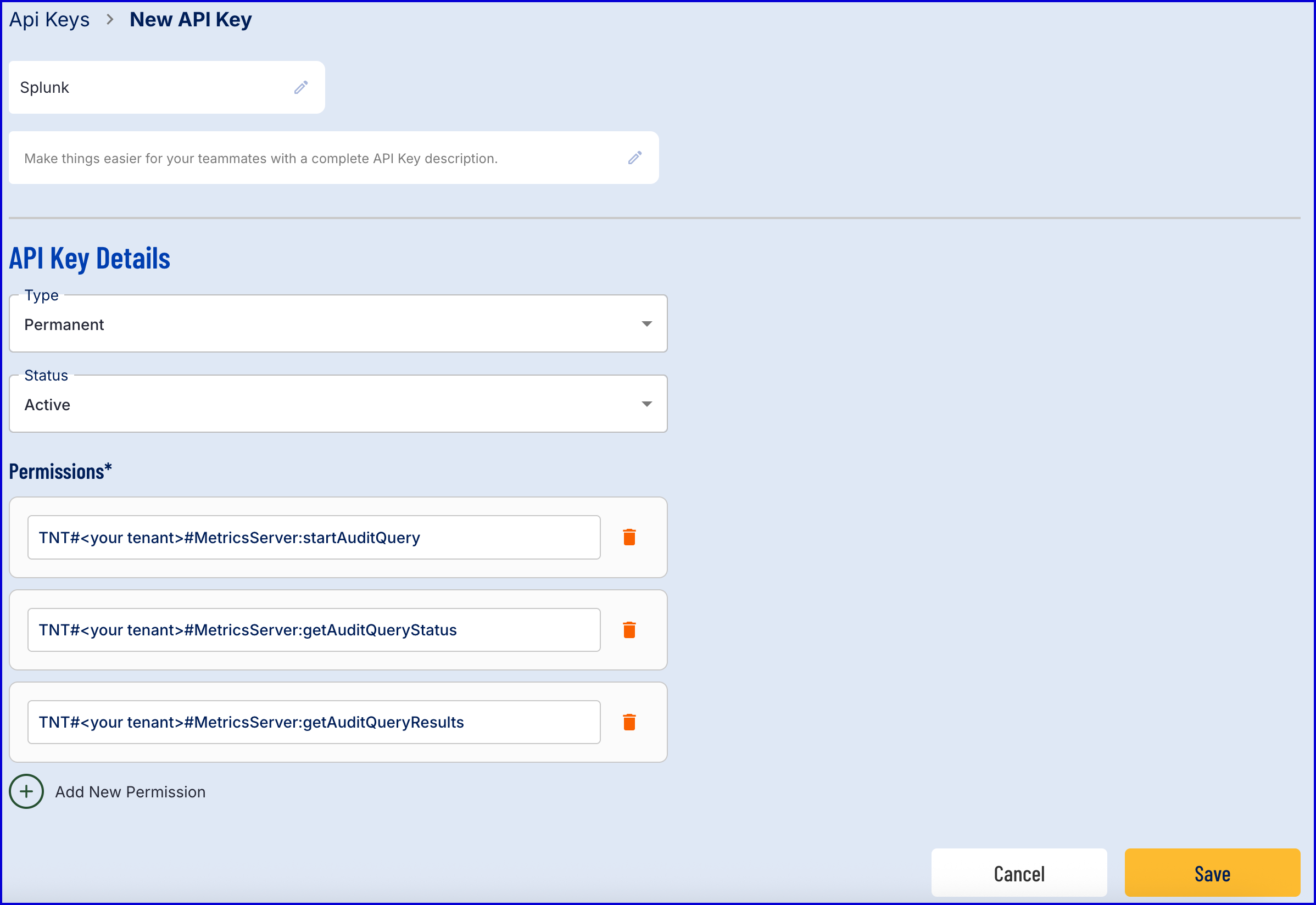
- Click the 'Save' button to finalize the API key creation.
Step 2 - Configure Splunk Cloud
This step will describe the configurations in Splunk Cloud to create a dedicated index for TrustX and a HTTP Event Collector (HEC) token.
Step 2.1 Create a Dedicated Index
- Log in to the Splunk Cloud dashboard and navigate to Settings > Indexes > New Index.
- Name the new index "trustx".
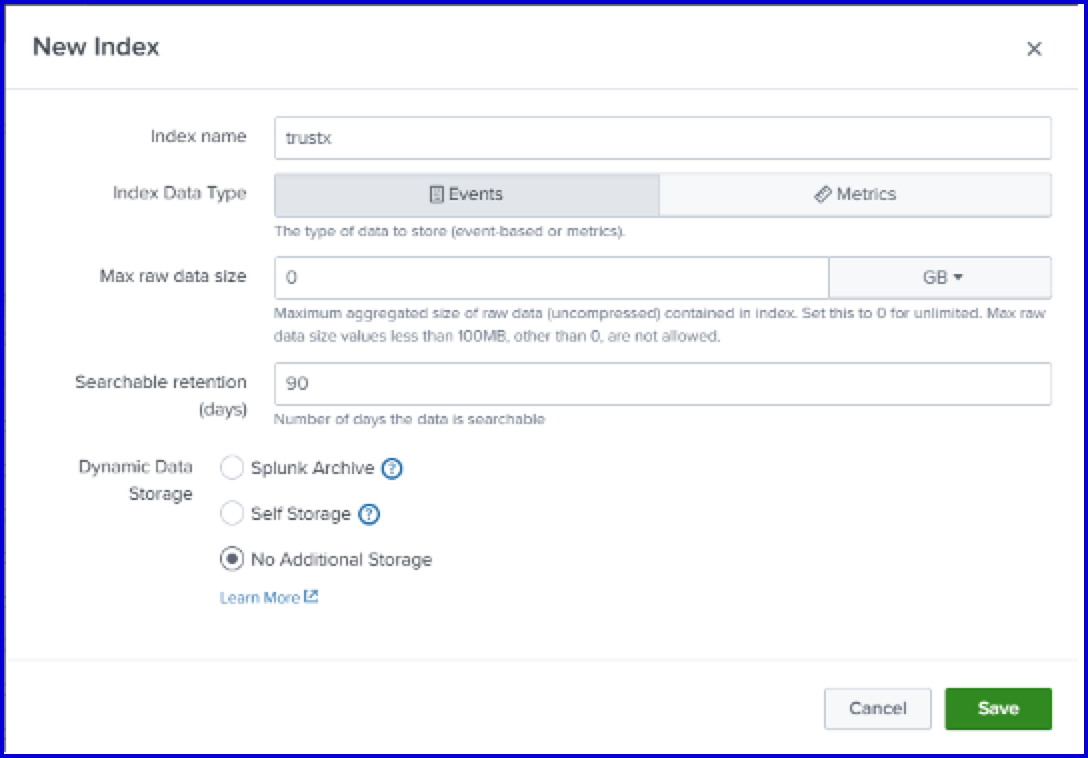
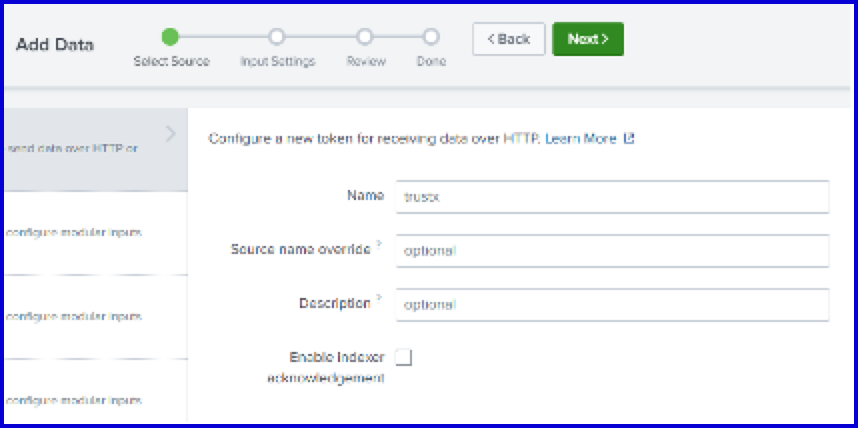
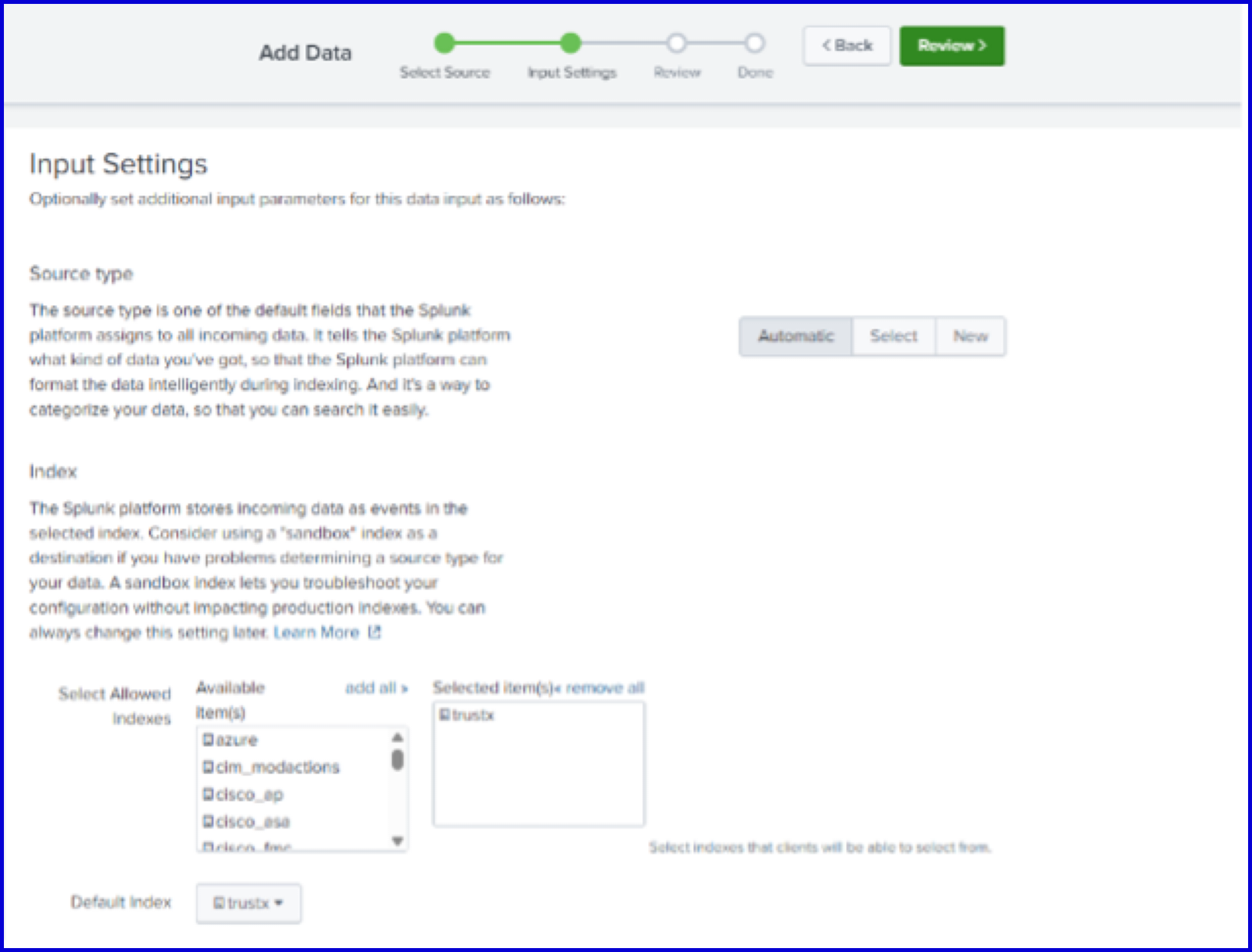
2.2 Create HEC Token
Navigate to Settings > Data Inputs > HTTP Event Collector > New Token.
Set the name and index accordingly:
- Name: "trustx"
- Index: "trustx"
Step 3 - Configure the Script
This section will describe configuring the .env file to include the keys created in Steps 1 and 2 of this guide.
- Edit your .env configuration file to include the following:
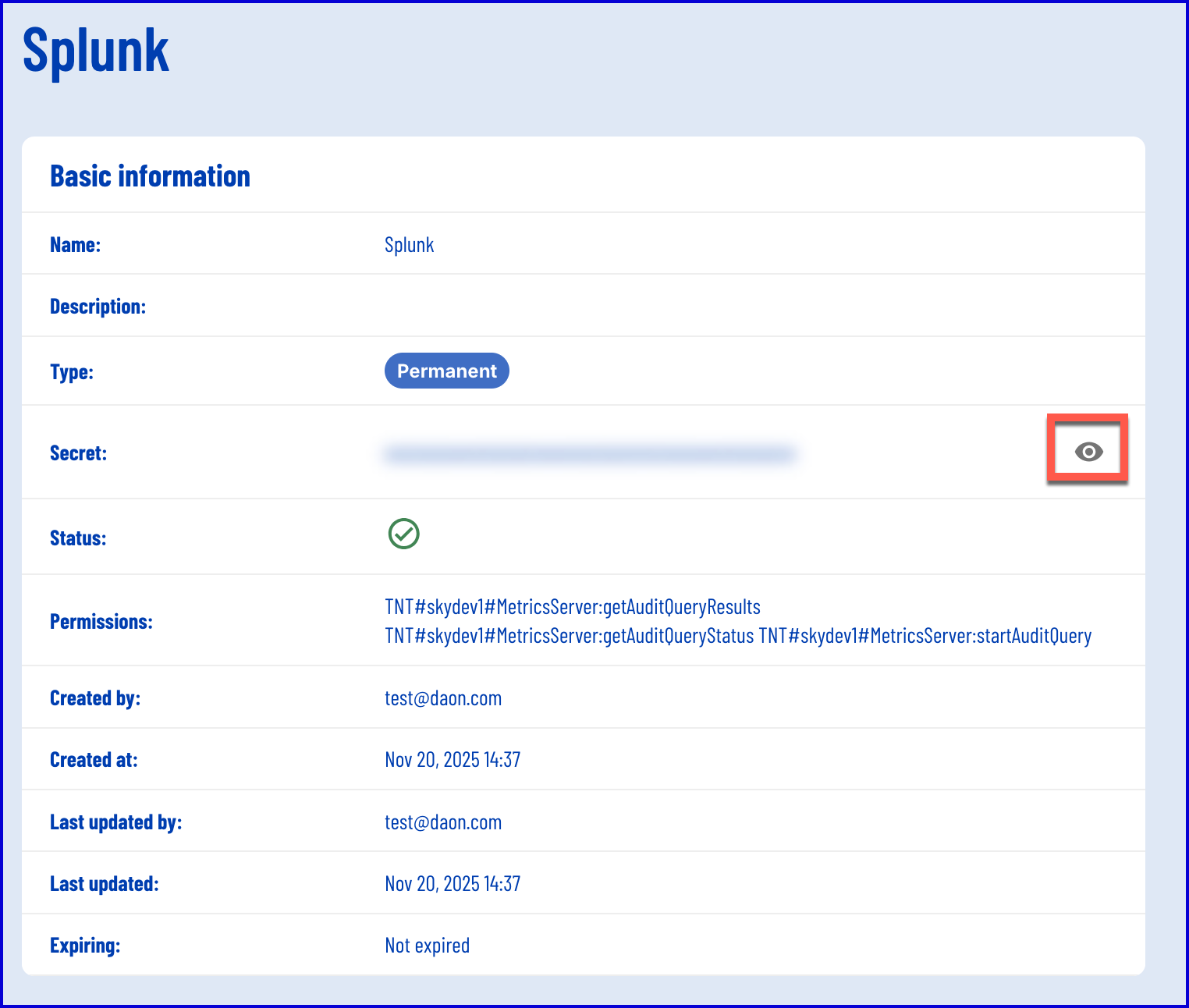
TRUSTX_API_KEY=<paste your TrustX API key secret here>TRUSTX_TENANT_HOST=<your_tenant>.oak.trustx.comSPLUNK_URL=https://http-inputs-<your_tenant>.splunkcloud.com:443/services/collectorSPLUNK_HEC_TOKEN=<paste your Splunk HEC token here>- To find your TrustX API key secret, navigate to the API Keys page in the TrustX Backoffice.
- Find the API Key created in Step 1 and select the magnifying glass under the 'Actions' column.
- Click the 'eye' icon to show the API secret.
- Place the “trustx_ingest” directory in /opt/splunk/bin/scripts/ on Splunk Heavy Forwarder (make sure that script is executable and that host can reach both TrustX Backoffice and Splunk Cloud).
- Schedule the script to run every 10 minutes.
Example:
crontab -e*/10 * * * * /usr/bin/python3 /opt/splunk/bin/scripts/trustx_ingest/trustx.py >> /var/log/trustx.log 2>&1Step 4 - Validate Ingestion in Splunk
This step will describe how to view the ingested reports in Splunk.
- Navigate to the Search & Reporting page in Splunk.
- Run the following search query: index=trustx
- The audit events from TrustX will be returned in the output of the search query.